Security company Volexity has recently encountered more and more new malware that uses interesting techniques to access victims’ emails from Gmail and AOL.
They called the malware “Sharpext”. It comes from a group called SharpTongue, also known as Kimsuke.
This is a North Korean group that specifically pursues nuclear weapons targets or other areas that North Korea considers to be in its national interests. Targets are located in Europe, the United States and South Korea.
Steals emails, but not passwords
Sharpext does not attempt to steal usernames or passwords, but instead sends emails and data from the user’s account to third parties.
The attack begins by tricking the user into opening an infected document that gives the attacker access to install Sharpext, a Chromium browser plug-in.
So far, such has been found in both Chrome and Edge, as well as a lesser known browser in South Korea called Whale. They are all built on Chromium.
Currently, only browsers in Windows have been attacked, but according to Volexity, in theory, there is nothing to prevent Chromium-based browsers in Linux and macOS from attacking Sharpext.
innovative method
What’s smarter about Sharpext is that one of the first things it does after installation is to kill running processes and replace some browser configuration files.
These files usually contain data that the browser checks to determine if someone has tampered with its settings. However, Sharpext has been able to replace these files with its own, so that looks fine when the browser runs its own scan procedure.
Creating such files outside of the browser itself is far from complicated, that the browser accepts them as real, but SharpTongue has managed that.
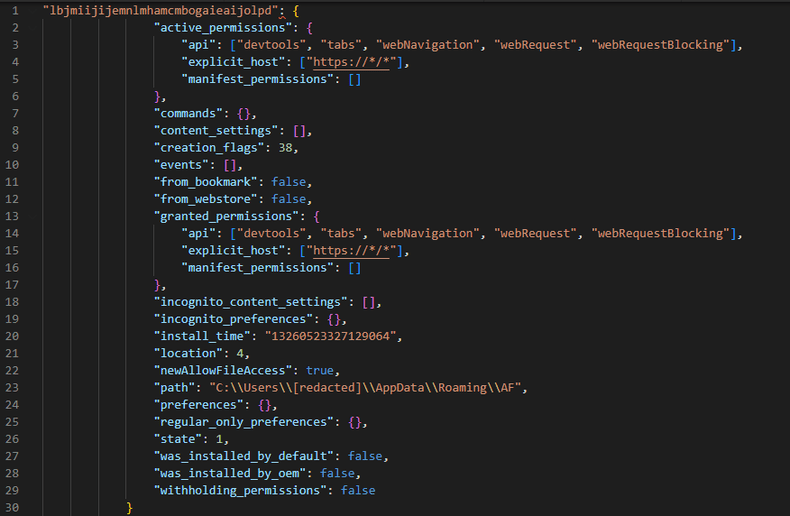
These fake files also contain a lot of the same files of the users, to disguise that the files have been overwritten by other files. All clear settings remain as before.
Once these files are in place, the script sends a command to the browser, one character at a time. Normally, the browser realizes this and warns the user that something like this is about to happen, with a warning in a popup. However, Sharpext monitors this and hides the window before it is displayed.
The command sent is equivalent to “Control + Shift + J”, which launches the DevTools panel in the browser. This is enabled but hidden by Sharpext, so the user probably won’t even notice it’s active.
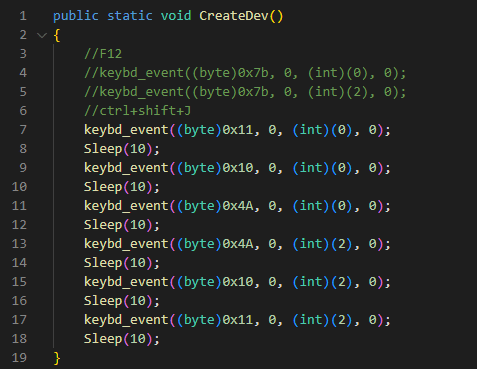
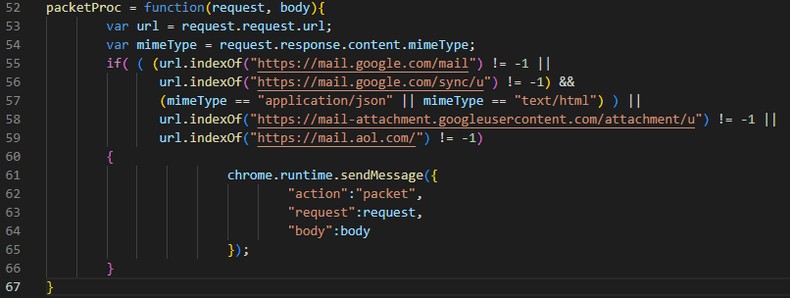
Then DevTools runs files that monitors open tabs in the browser and gathers information from them.
Since emails and attachments are stolen from a logged-in session, the attack is also hidden from the email client’s service provider. Everything seems to be normal, which makes it very difficult to detect the attack.
constantly improving
Previous versions of Sharpext were full of bugs, but the current version is 3.0 and many of these bugs have been fixed. Not only that, the latest version has also been optimized so that it retrieves code from an external server instead of putting everything locally on the infected machine.
This way, the attacker doesn’t have to update the malware – he only retrieves his own updated code – and in addition, there is minimal code that can be found locally for security software that eavesdrops on signs of infection.
According to Volexity, the fact that bugs have been fixed, algorithm improvement and functionality expanded, indicates that attackers have constantly taken advantage of the attacks and information obtained with the help of Sharpext.
Sharpext can eventually do the following:
- Create a list of email previously collected from the victim to ensure that duplicates are not loaded. This list is constantly updated when Sharpext is launched.
- Create a list of email domains that the victim has already contacted. This list is constantly updated when Sharpext is launched.
- Create a blacklist of email senders to ignore when collecting email from the victim.
- Add a domain to the list of all domains the victim has viewed.
- Upload a new attachment to the remote server.
- Upload Gmail data to the remote server.
- Create a list of attachments to extract.
- Upload AOL data to the remote server.
Altogether, thousands of emails have been stolen and sent to North Korea, he writes Volexity in her report.
Recommended countermeasures
Volexity recommends the following to detect and/or prevent attacks of this type:
- Turn on logging of scripts that are running or that are blocked.
- Regularly check for plugins on people and machines that are logical targets.
- Block Sharpext gonamod.com, siekis.com and worldinfocontact.club servers.

“Web specialist. Lifelong zombie maven. Coffee ninja. Hipster-friendly analyst.”