A computer attack discovered in Norway helped expose a larger campaign targeting, among others, the defense sector and public institutions.
Last summer, it became known that 12 ministries were subjected to a cyber attack. The attackers used previously unknown vulnerabilities to break in, and were operating secretly for months before they were discovered.
What distinguishes these security vulnerabilities is that they were discovered in Norway. This is where it was first seen in use, says Martin Albert Hof, who heads the National Cybersecurity Center.
The centre, affiliated with the National Security Service (NSM), coordinates work to defend Norway against computer attacks. Here they collect information about computer attacks, coordinate incident response, and share information further. Information is often shared only with a closed group, but sometimes the NSM expands.
In cooperation with its American counterpart CISA, NSM published Technical description What vulnerabilities were exploited and how organizations can look for signs of compromise.
As for the NRK, the NSM can now find out what the information exchange led to.
– Albert Hof says: – There have been many companies in Norway and internationally that have been affected by the current vulnerabilities in Ivanti and our extensive information sharing has contributed to many companies exposing ongoing compromise and avoiding compromise attempts.
In Norway, a single-digit number of companies were hacked, according to NSM. They were, among others, within the defense sector and the public sector.
Albert Hof says dozens of Norwegian companies had vulnerabilities that could be exploited. NSM first notified target organizations it knew were at risk, and looked extensively with CISA.
NSM also provided advice on how companies can protect themselves before a security update is available from the manufacturer.
– The number of people at risk could have been much higher if the necessary measures had not been taken, concludes Albert Hof.

DN has been mentioned previously Many companies were affected.
But it is still unknown who is behind the attack PST previously told NRK It is likely that the attack on the ministries was carried out on behalf of a state.
Albert Hof says it is essential to stop computer attacks at an early stage.
-The earlier you can stop it, the less damage it will do. We have seen examples where settlements have occurred for a long time and then you can only imagine what the actor can gain from it.
It uses three unknown vulnerabilities
The computer attack targeted IT systems of the Departmental Security and Services (DSS) organisation. When abnormal activity was detected, two businesses, Microsoft and Mnemonic, were linked.
Hackers used a variety of methods and tricks to break into ministries' computer systems and cover their tracks.
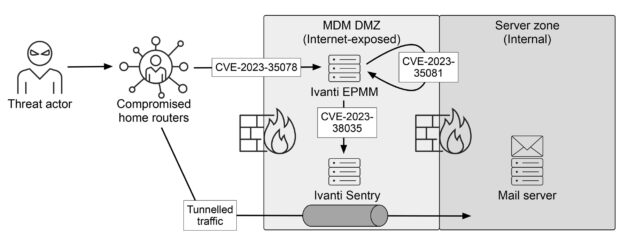
The most important of which was the exploitation of three zero-day vulnerabilities in software at Ivanti. This company provided two programs for ministries – one to control mobile devices (Ivanti EPMM) and one to sync email with them (Ivanti Sentry).
This zero-day vulnerability means that neither Ivanti nor the security community knew about the vulnerability before a malicious actor exploited it.
The attackers also used compromised home routers in Norway to carry out the attack so that their activity would be placed under the radar and bypass geo-blocking. They have also erased their traces, making activity more difficult to detect.
Norwegian security company Mnemonic found the three vulnerabilities that were exploited. The two company employees who discovered the third vulnerability, Erlend Leiknes and Tor E. Bjørstad, recently lectured about the work at the NDC Security conference.

These vulnerabilities are often surprisingly simple if you look in the right place, Bjorstad said.
He warned in the lecture that outdated and obscure IT solutions represent fertile hunting grounds for threat actors, and that these systems have often not been examined thoroughly enough by security researchers.
Recently it became known The vulnerabilities were abused in other Ivanti product series in Norway. On LinkedIn Bjorstad calls it “déjà vu.” “These vulnerabilities are incredibly similar to the zero-day vulnerabilities that emerged last summer,” he wrote.
Updated at 08:09: Added that Mnemonic found all three vulnerabilities.

“Explorer. Unapologetic entrepreneur. Alcohol fanatic. Certified writer. Wannabe tv evangelist. Twitter fanatic. Student. Web scholar. Travel buff.”




