Real-time manipulation
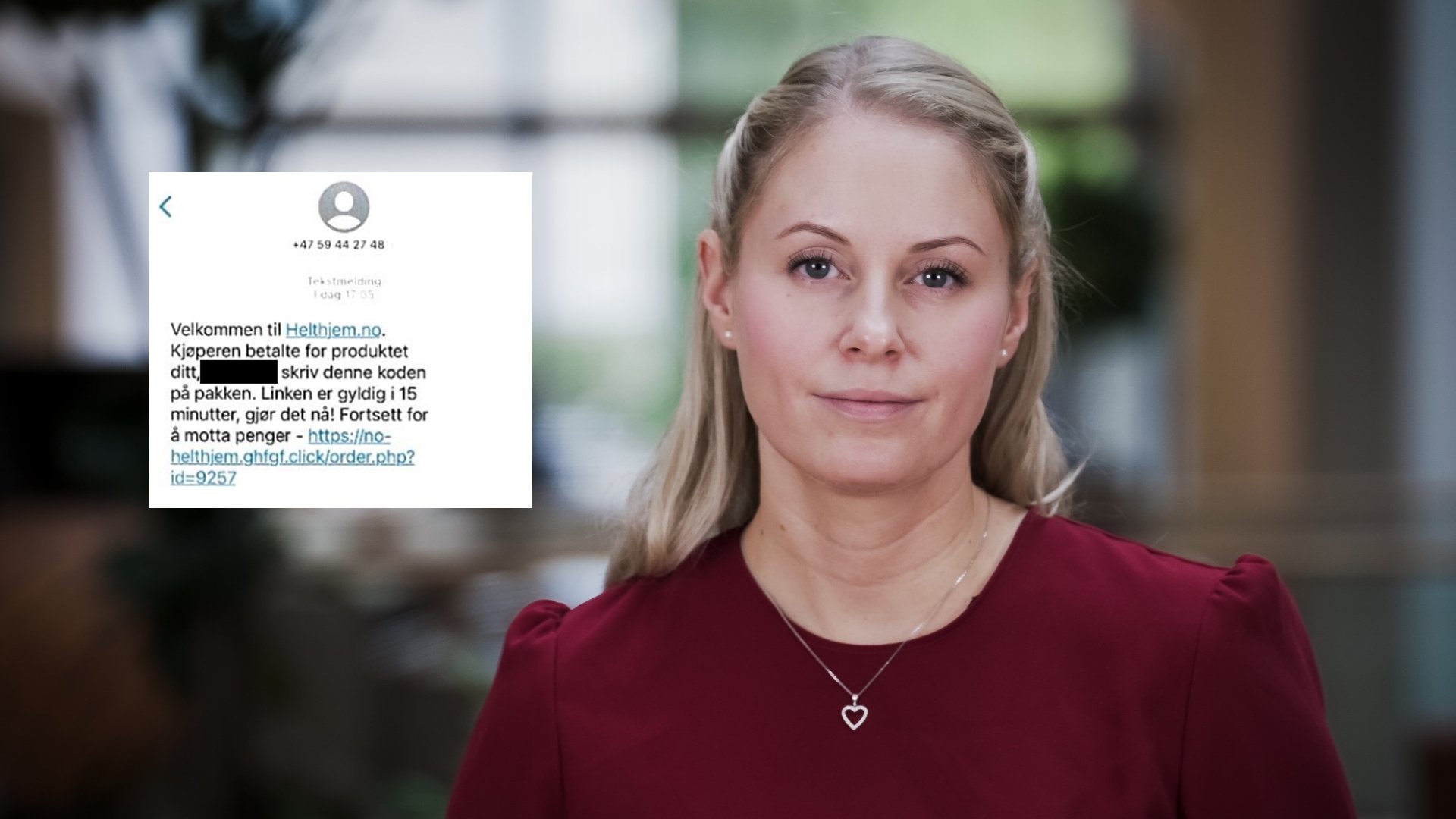
Such an attack can start with the victim receiving an SMS and/or a call.
– In both cases, criminals hid behind fake mobile or landline phone numbers or Sender’s name – for example, the name of the bank or the like. In SMS or in conversation, says Torbjørn Busch, it is usually played on the basis of fear of being put on a glue stick and acting irrationally.
An example of a message you might receive is “The bank suspects there is unauthorized activity on your account.”
– Such a letter will too It causes you stress and noticeable time pressure as the victim must take quick action to prevent abuse and loss money. Criminals want you to get carried away with fear, bite the hook and click on a link Thought it leads to the online bank. What you think is the official login page of the bank is actually a malicious page Criminal Watch Site. A website can look just like the login page you usually log in to You are on.
Scammers want you to give away your login information, bank ID, Activation codes or other one-time use codes.
– When you enter the one-time code from BankID on the fake website, scammers can read it. Since they also have their date of birth, they can quickly log in, for example, to the real online bank sooner The code becomes very old. This is possible because the perpetrators are ready, in real time, and follow everything you write on the fake The site – which they control. Once they enter the online bank, they are happy to start the transfer of money out of your account, Busch says.
– But since such transfers often require separate approval via BankID, it may let you believe it Your “login” failed. When you then try to “login” again with a new BankID code, you have i Really looking at the scammers the code they need to allow the transfer out of the account.
– Another alternative could be that you receive a call, or you are tricked into taking back the “bank”.
– over here One can be asked to “verify their identity” with BankID that makes criminals, while they do You’re on the topic, you may have drained your account of money. BankID can also act as an activation code So that criminals themselves can install the bank app on their own phones, and then execute it Payments from the account they received.
Jailbreak
– Phones are delivered from suppliers with access restrictions. These restrictions are often measures To secure your phone and its data. Jailbreak means that you unlock the phone using software To increase access to oneself as a user, this may involve security risks. ¨
Apps on the phone can gain increased access and adjust settings.
Small vulnerabilities with little impact can turn into serious vulnerabilities. In practice you have One part of the security measures on the phone is destroyed which usually makes the phone smaller vulnerable. One can compare security measures to onions as each layer forms a security barrier. When you jailbreak the phone, only the casing is left.
0 day attack
0-day (zero-day) attack means that the vulnerability in the program is unknown and is patched The attacker is the only one who knows the vulnerability. To protect against these vulnerabilities It’s tricky, and the attacker can give full access to the phone without the user being able to protect themselves.
These types of vulnerabilities are not often found, and they are fixed as soon as they become known, according to the expert.
– But once they are Known, many will benefit from the type of attack. This is why it is important to keep your phone up to date Known vulnerabilities cannot be used against the phone. Criminals may take advantage The vulnerability to control the mobile phone, the online bank may become vulnerable to attacks. The attacker was given The so-called “system privileges” where there are no restrictions on what criminals can do mobile.
Download unsigned apps from rogue markets
– In order for the application to be installed on the phone, it must be certified / certified by Apple or Google, by phone. Unauthorized application can be installed by allowing the user Unsigned applications. The user can then download from sources other than the App Store and Google Play Store. This is a major security risk because apps downloaded from other sources don’t carry the same thing Quality control and check for malicious content. The apps can then be turned into Trojans, that is, they give up It seems to be some kind of app, but it’s actually something else.
typical for such games as iBackground steals user information, photos and data. By allowing unsigned apps, that’s a lot Easier to get the user to install a malicious app – like Flubot, says expert.
– Flobot It is an example of a malicious application, which is actually ABInstall Trojans, which are designed to steal information from the phone and spread the virus further via SMS or multimedia messages.
An unsigned application, or an application that has been granted too many rights on the phone either by the user Or exploiting the platform, could steal information from the phone, Busch asserts.
– They can act like one A legit app that offers services and functions as expected, but actually sends data and passwords Names of all information for criminals. In addition, there are other ways in which they can steal information such as For example, screenshot, keystroke recording, microphone and camera use, and transmission Network traffic from legitimate applications to attackers who can manipulate it.
private bank systems
A more complex, but not unlikely, attack surface is the bank’s systems themselves. Then you can think about it Attackers can send SMS from the bank, block SMS from the bank, send phishing links or make transactions. These types of attacks are as dangerous and threatening as possible affect a lot. Here you have to trust the bank and its security staff to find and stop the mailFinal attacks.
Source: Telenor

“Explorer. Unapologetic entrepreneur. Alcohol fanatic. Certified writer. Wannabe tv evangelist. Twitter fanatic. Student. Web scholar. Travel buff.”