Hacking Microsoft BitLocker, the encryption technology used in Windows, takes less than a minute.
Steals keys with cheap tools for 50 NOK
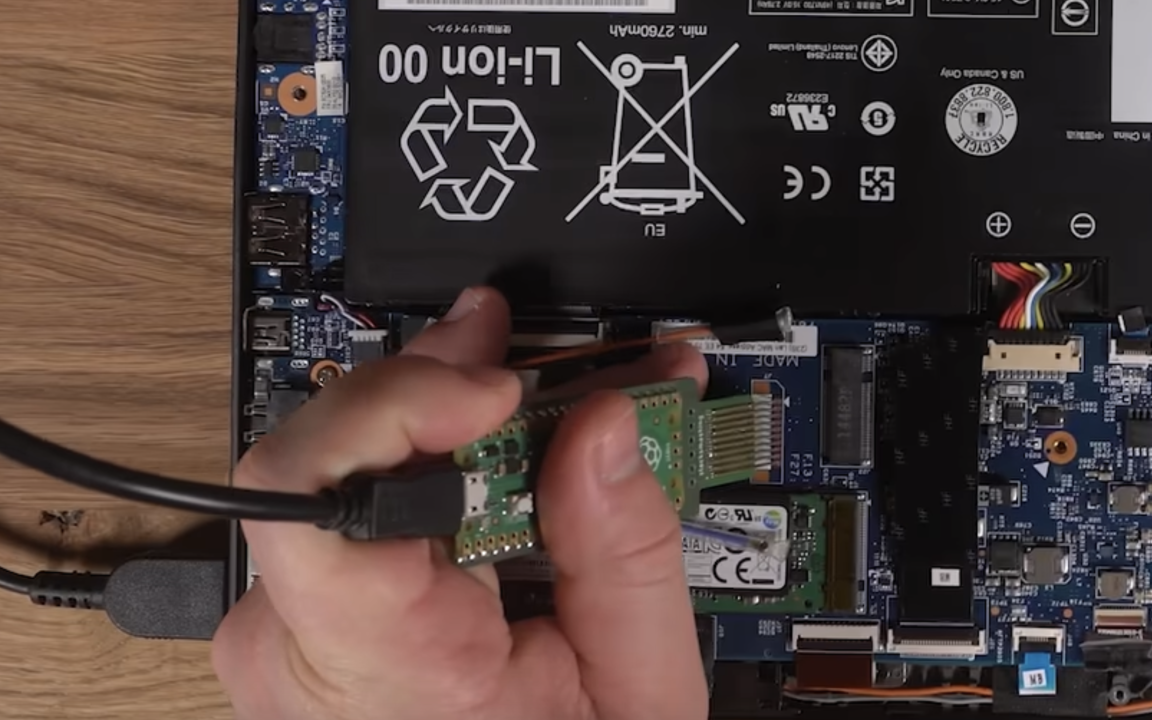
Not only that, the only thing needed is a Raspberry Pi Pico which costs just over 50 NOK. He's YouTuber “stacksmashing” who demonstrates how to steal encryption keys on Windows laptops. Thus decrypting the content. How long did it take? 43 seconds, and with a very simple device that only reads circuit board information.
There is a flaw in the Trusted Platform Module, or TPM if you will, and it is being exploited. Note that hacking requires physical access to the device, which is unlikely to be a problem if the hacker really wants access: if the device can be physically stolen, it won't take much time to open it and steal the encrypted keys stored in the device. TPM.
This is very simple
Microsoft has acknowledged that such attacks are possible, but believes advanced equipment is needed. It is true that more than one is required Machine To perform a hacking operation, but hackers who know what they are doing can use simple tools and perform the hacking process quickly.
In any case, the hole must be repaired, because as you can see from the video below, it is the poor hardware design that makes it possible to retrieve the keys. “stacksmashing” was found on an old Lenovo laptop, an LPC bus that was not in use. Such a connection is a low speed connection such as eg. Used to connect BIOS ROM to CPU. Once the hacker found the connector next to the M.2 SSD, all he had to do was connect the Raspberry Pi Pico to the pins on the unused connector to extract the keys that unlock the drive. This is because the Pi retrieves the binary sets from the TPM during device startup.

“Web specialist. Lifelong zombie maven. Coffee ninja. Hipster-friendly analyst.”